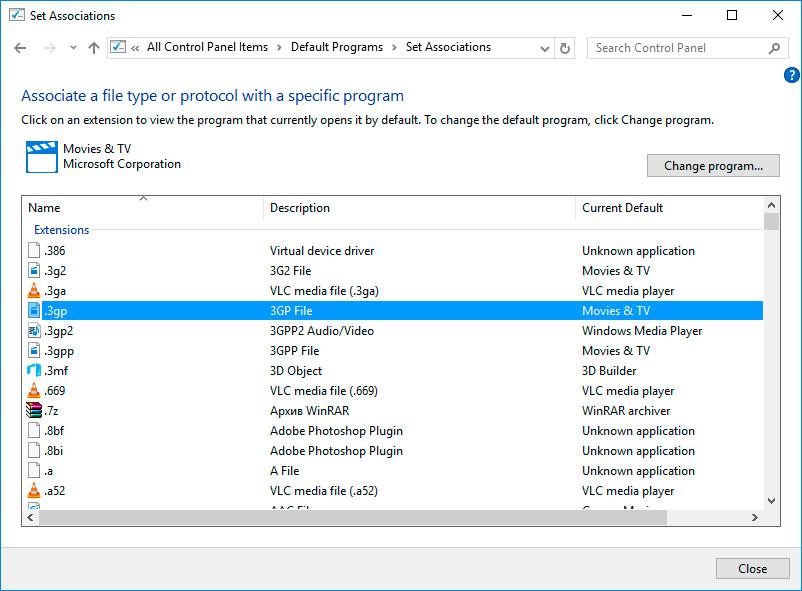
Lnk file parser. Contribute to EricZimmerman/Lnk development by creating an account on GitHub. And even trying the 'open with' on a pdf file, it also is not on the options list, and navigating to the.lnk file (the shortcut in the start menu), that won't do an association either - First the link is not shown, and then in the chooser window selecting 'all file types', it shows up, but selecting it responds, 'This app cannot run on your PC'. The current default for.lnk is 'Unknown Application' but if I select 'Change Program' the only option available is 'Look for an App in the App Store' however, if I locate and select 'explorer.exe' in the Windows folder it freezes the 'set associations' window. Here is the list of file association fixes (Windows defaults) for some of the common file types. These registry fixes are applicable for Windows® 10 only. AVI IMG TXT BAT INF URL BMP JPE/JPEG/JPG VBS CHM JS WMA CMD LNK WMV COM MP3 XML EXE PNG ZIP GIF REG Directory.
Specifies the Shell Link Binary File Format, which containsinformation that can be used to access another data object. The Shell LinkBinary File Format is the format of Windows files with the extension'LNK'.
This page and associated content may be updatedfrequently. We recommend you subscribe to the RSSfeed to receive update notifications.
Published Version
Date | Protocol Revision | Revision Class | Downloads |
|---|---|---|---|
9/12/2018 | 5.0 | Major | PDF | DOCX | Diff |
Previous Versions
Date | Protocol Revision | Revision Class | Downloads |
|---|---|---|---|
9/15/2017 | 4.0 | Major | PDF | DOCX | Errata | Diff |
6/1/2017 | 3.0 | None | PDF | DOCX | Diff |
7/14/2016 | 3.0 | None | PDF | DOCX | Diff |
10/16/2015 | 3.0 | None | PDF | DOCX |
6/30/2015 | 3.0 | Major | PDF | DOCX |
5/15/2014 | 2.0 | None | PDF | DOCX |
2/13/2014 | 2.0 | None | PDF | DOCX |
11/14/2013 | 2.0 | None | PDF | DOCX |
8/8/2013 | 2.0 | Major | PDF | DOCX |
1/31/2013 | 1.2 | None | |
10/25/2012 | 1.2 | None | |
7/12/2012 | 1.2 | None | |
3/30/2012 | 1.2 | None | |
12/16/2011 | 1.2 | None | |
9/23/2011 Muse all albums download. | 1.2 | None | |
6/17/2011 | 1.2 | Minor | |
5/6/2011 | 1.1 | None | |
3/25/2011 | 1.1 | None | |
2/11/2011 | 1.1 | None | |
1/7/2011 | 1.1 | None | |
11/19/2010 | 1.1 | None | |
10/8/2010 | 1.1 | None | |
8/27/2010 | 1.1 | Minor | |
7/16/2010 | 1.0 | New |
Preview Versions
From time to time, Microsoft maypublish a preview, or pre-release, version of an Open Specifications technicaldocument for community review and feedback. To submit feedback for a previewversion of a technical document, please follow any instructions specified forthat document. If no instructions are indicated for the document, pleaseprovide feedback by using the Open Specification Forums.
The preview period for a technical document varies.Additionally, not every technical document will be published for preview.
A preview version of this document may beavailable on the WindowsProtocols - Preview Documents page. After the preview period, themost current version of the document is available on this page.
Development Resources
Findresources for creating interoperable solutions for Microsoft software,services, hardware, and non-Microsoft products:
Plugfestsand Events, Test Tools,DevelopmentSupport, and Open SpecificationsDev Center.
Intellectual Property Rights Notice for Open Specifications Documentation
Technical Documentation. Microsoft publishes Open Specificationsdocumentation (“this documentation”) for protocols, file formats, dataportability, computer languages, and standards support. Additionally, overviewdocuments cover inter-protocol relationships and interactions.
Copyrights. This documentation is covered by Microsoftcopyrights. Regardless of any other terms that are contained in the terms ofuse for the Microsoft website that hosts this documentation, you can makecopies of it in order to develop implementations of the technologies that aredescribed in this documentation and can distribute portions of it in yourimplementations that use these technologies or in your documentation asnecessary to properly document the implementation. You can also distribute inyour implementation, with or without modification, any schemas, IDLs, or codesamples that are included in the documentation. Hachiko full movie hindi dubbed download. This permission also applies toany documents that are referenced in the Open Specifications documentation.
No Trade Secrets. Microsoft does not claim any tradesecret rights in this documentation.
Patents. Microsoft has patents that might cover yourimplementations of the technologies described in the Open Specificationsdocumentation. Neither this notice nor Microsoft's delivery of this documentationgrants any licenses under those patents or any other Microsoft patents.However, a given Open Specifications document might be covered by the MicrosoftOpen SpecificationsPromise or the Microsoft CommunityPromise. If you would prefer a written license, or if thetechnologies described in this documentation are not covered by the OpenSpecifications Promise or Community Promise, as applicable, patent licenses areavailable by contacting iplg@microsoft.com.
License Programs. To see all of the protocols in scopeunder a specific license program and the associated patents, visit the Patent Map.
Trademarks. The names of companies and products containedin this documentation might be covered by trademarks or similar intellectualproperty rights. This notice does not grant any licenses under those rights.For a list of Microsoft trademarks, visit www.microsoft.com/trademarks.
Fictitious Names. The example companies, organizations,products, domain names, email addresses, logos, people, places, and events thatare depicted in this documentation are fictitious. No association with any realcompany, organization, product, domain name, email address, logo, person,place, or event is intended or should be inferred.
Reservation of Rights. All otherrights are reserved, and this notice does not grant any rights other than asspecifically described above, whether by implication, estoppel, or otherwise.
Tools.The Open Specifications documentation does not require the use of Microsoftprogramming tools or programming environments in order for you to develop animplementation. If you have access to Microsoft programming tools andenvironments, you are free to take advantage of them. Certain OpenSpecifications documents are intended for use in conjunction with publiclyavailable standards specifications and network programming art and, as such,assume that the reader either is familiar with the aforementioned material orhas immediate access to it.
Support.For questions and support, please contact dochelp@microsoft.com.
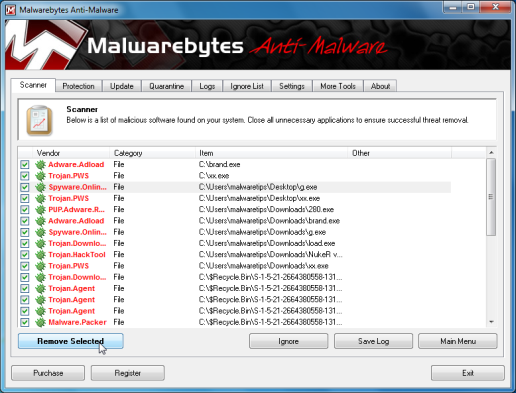
Malware
We have seen an increase in attacks that leverage malicious LNK files that use legitimate apps—like PowerShell—to download malware or other malicious files.
Update as of May 30, 2017, 5:00 AM CDT to update the date referencing Trojan downloaders that used .zip files within .zip files from '2016' to '2017'.
PowerShell is a versatile command-line and shell scripting language from Microsoft that can integrate and interact with a wide array of technologies. It runs discreetly in the background, and can be used to obtain system information without an executable file. All told, it makes an attractive tool for threat actors. There were a few notable instances where cybercriminals abused PowerShell: in March 2016 with the PowerWare ransomware, and in a new Fareit malware variant in April 2016. Because this seemed to be an upward trend, security administrators became more familiar with how to prevent PowerShell scripts from doing any damage.
However, cybercriminals are staying ahead of the curve by using alternative means of executing PowerShell script—Windows LNK (LNK) extensions. LNK files are usually seen by users as shortcuts, and used in places like the Desktop and Start Menu. LNK was actually already used as an attack vector as early as 2013. And in early 2017, we noted how Trojan downloaders used a .zip within a .zip to disguise a LNK file attachment that led to the Locky ransomware.
Now, we’re seeing an increase in attacks that leverage malicious LNK files that use legitimate apps—like PowerShell—to download malware or other malicious files. To illustrate how the trend of using LNK files is rising, note how one single LNK malware (identified by Trend Micro as LNK_DLOADR.*) has had a significant jump in detections since January 2017. The steep rise shows how popular this method is becoming:
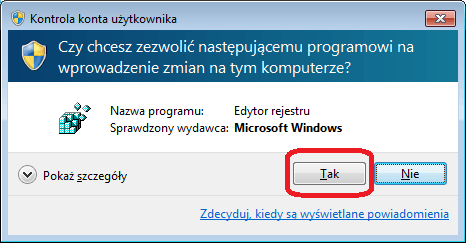
Figure 1. Detected LNK_DLOADR over a 4 month period
Recent LNK-PowerShell and ChChes attacks
In October 2016 we saw attackers using the combination of LNK, PowerShell, and the BKDR_ChChes malware in targeted attacks against Japanese government agencies and academics. The attack used a fake .jpg extension to camouflage the malicious PowerShell file.
Figure 2. Attack used to compromise Japanese targets in October 2016
In January 2017 we spotted the group APT10 (also called MenuPass, POTASSIUM, Stone Panda, Red Apollo, and CVNX) using a similar attack for a wide-spread spear phishing campaign. In this version, the LNK file executes CMD.exe, which in turn downloads a fake .jpg file hiding the malicious PowerShell script.
The group has continued to evolve their cyberespionage activities, and in April 2017 they used a similar strategy to also download BKDR_ChChes, which is a popular malware used in targeted attacks.
New LNK-PowerShell attacks
We identified one campaign, likely still ongoing, that has a new and complicated LNK strategy. These attackers seem to be using several layers of command line, built-in, Windows tools. They send a phishing email with lures that push the victim to “double click for content”, typically a DOCX or RTF file embedded with a malicious LNK. Instead of directly executing PowerShell, the LNK file will execute MSHTA.exe (a file used for opening HTML applications), which executes a Javascript or VBScript code that in turn downloads and executes the PowerShell script. The PowerShell then executes a reverse shell (like Metasploit or Cobalt Strike) to complete the compromise.
Figure 3. Complex LNK attack leveraging MSHTA.exe files
Last month we identified another spear phishing campaign also using a combination of LNK and PowerShell. Unfortunately, the Command and Control (C&C) server where the main payload was stored is no longer accessible.
Their strategy seems to have fewer layers: the LNK file is embedded in a document file and if a user double clicks to open the message, it executes a PowerShell file (or a similar Windows command line tool) to download another script. The other script then downloads the main payload.
Figure 4. A less complicated LNK-PowerShell attack
We believe this specific attack may be politically motivated due to the economic and controversial subject of the decoy document. However, a full analysis is tricky because the trail ends when one of the C&C servers dies. Without the full picture, it is difficult to associate this type of attack to known campaigns.
Hidden LNK commands
In many cases, these malicious LNK files can reveal valuable information about the attacker’s development environment. To help get this information, a quick analysis is possible by viewing the properties of the file.
However, we are encountering cases where the command line argument is so long that it is no longer fully visible in the Properties > Shortcut window. When viewed, only the target application (CMD.exe, MSHTA.exe, and other non-malicious command line applications) is seen.
.lnk File Association
Figure 5. Only the target application is visible
Our tests revealed that the maximum length for Shortcut > Properties > Target is only 260 characters. Anything longer than that will not be visible. However, the maximum length for a command line argument is 4096 characters.
Lnk File Fix
The attacker actually pads several spaces or newline characters before the malicious argument. Using a parser tool reveals that it is much longer (figure 6), though it still works normally:
Figure 6. Padded file hiding malicious code
Attackers take advantage of this to try and disguise or hide the malicious portion of the code. This padding strategy may prevent a quick analysis of a LNK file, but any LNK parser can still extract the arguments without any problem.
Recommendations and best practices
Malware developers continue to upgrade their tools and look for different ways to deliver their malicious payloads. Leveraging these LNK files is another strategy, but there are ways to prevent and mitigate these threats:
- Upgrading PowerShell to version 5, which is available as part of the Windows Management Framework and included on Windows 10, is recommended. Using Group Policy to turn on logging makes it easier to check for breaches.
- Users and enterprises alike should be wary of executable files received through email. Most files ending in *.EXE are auto-rejected on an email server, but if security is a concern then administrators should consider adding *.LNK to the list
- It is similarly not advisable to open any LNK file received via email (or from anywhere outside your machine).
To identify if it is a LNK file or not:
- If inside an archive (e.g. WinRAR, WinZip), the LNK extension is clearly visible, as well as the “Type” (it says “Shortcut”).
- For any Windows folder, you have to modify the registry if you want LNK files to be displayed. A small overlay arrow icon pointing to the upper right is one of the identifiers of a LNK file. Another way to do this: switch the Windows folder to “Details View”, then check the “Type”.
- For LNK embedded in Word documents, users have to be aware of these types of attacks to know what to look for. The bottom line is: never open these kinds of documents without verifying the source. If your organization does not need any packager objects, then there is a way to disable the feature totally by editing the registry.
Trend Micro™ Smart Protection for Endpoints with Maximum XGen™ security infuses high-fidelity machine learning into a blend of threat protection techniques to eliminate security gaps across user activity and any endpoint—the broadest possible protection against advanced attacks.
Trend Micro™ Deep Discovery™ provides detection, in-depth analysis, and proactive response to today’s stealthy malware and targeted attacks in real-time. It provides a comprehensive defense tailored to protect organizations against targeted attacks and advanced threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack lifecycle, allowing it to detect threats, even without any engine or pattern update.
